A single cyber breach can cost a south-african e-commerce company over $3 million in lost revenue, fines, and damaged reputation. For IT managers striving to protect sensitive customer data, the challenge goes far beyond technology choices. Understanding the real-world risks and requirements of modern cybersecurity empowers businesses to build trust, achieve compliance with strict European and South African regulations, and stay ahead of evolving threats.
Table of Contents
- Defining Cybersecurity For Modern Businesses
- Major Cyber Threats Facing E-commerce Firms
- POPIA, GDPR And Global Compliance Duties
- Effective Defence Strategies And Best Practices
- Human Risk, Staff Training And Avoiding Mistakes
- Choosing Security Solutions For Business Needs
Key Takeaways
| Point | Details |
|---|---|
| Holistic Cybersecurity Approach | Modern businesses must adopt a comprehensive strategy that includes risk assessment, technological infrastructure, and personnel training to effectively mitigate cyber threats. |
| Proactive Training and Awareness | Continuous employee training programmes should be implemented to reduce human-related vulnerabilities and create a culture of cybersecurity within the organisation. |
| Compliance with Data Protection Regulations | South African businesses must ensure adherence to regulations like POPIA and GDPR, embedding data protection into core operational processes. |
| Dynamic Security Solutions | Organisations need to select tailored cybersecurity solutions that address specific vulnerabilities while ensuring scalability and integration with existing systems. |
Defining Cybersecurity for Modern Businesses
Cybersecurity represents a comprehensive strategic approach for protecting digital assets, networks, and systems from potential threats and vulnerabilities. At its core, cybersecurity encompasses the methodical protection of computer systems, networks, programmes, and data from digital attacks, breaches, and unauthorized access. Modern businesses must understand that cybersecurity is no longer just a technical concern but a critical business strategy involving technological, human, and organisational dimensions.
In contemporary digital environments, cybersecurity involves identifying, avoiding, managing, and mitigating risks associated with cyberspace ranging from human error to sophisticated state-sponsored attacks. This multifaceted discipline requires a holistic approach that goes beyond simple defensive technologies. Businesses must recognize that effective cybersecurity involves:
- Comprehensive risk assessment strategies
- Advanced technological infrastructure
- Robust personnel training programmes
- Continuous monitoring and adaptation
The contemporary definition of cybersecurity, as outlined in recent academic research, highlights its multidisciplinary nature. It is not merely about implementing firewalls or antivirus software but creating a resilient ecosystem that can anticipate, respond to, and recover from potential digital threats. Proactive cybersecurity means understanding potential vulnerabilities, developing sophisticated defence mechanisms, and maintaining an agile approach to emerging digital risks.
Pro tip: Conduct a comprehensive cybersecurity audit annually to identify and address potential vulnerabilities before they can be exploited by malicious actors.
Major Cyber Threats Facing E-commerce Firms
E-commerce businesses operate in an increasingly complex digital landscape where cyber threats continue to evolve at an alarming rate. Cybersecurity threats in e-commerce encompass a wide range of sophisticated attacks designed to compromise business operations and customer data. These threats are not just technical challenges but represent significant strategic risks that can potentially destroy customer trust and organisational reputation.
The most prevalent cyber threats facing e-commerce firms include:
- Phishing Attacks: Sophisticated social engineering techniques targeting employee and customer credentials
- Malware Infections: Destructive software designed to infiltrate and damage digital infrastructure
- Denial-of-Service (DoS) Attacks: Overwhelming systems to disrupt online business operations
- Personal Data Breaches: Unauthorized access and potential theft of sensitive customer information
Modern cyber threats have become increasingly complex, with emerging challenges including AI-enabled attacks and vulnerabilities from Internet of Things (IoT) devices. Attackers are constantly developing more advanced techniques to exploit technological and human vulnerabilities. E-commerce businesses must adopt a proactive and comprehensive approach to cybersecurity that goes beyond traditional defensive strategies.

Organisational resilience requires continuous investment in technological solutions, employee training, and adaptive security protocols. This means implementing robust encryption technologies, conducting regular security audits, maintaining up-to-date security systems, and creating a culture of cybersecurity awareness among all staff members.
Pro tip: Implement a mandatory quarterly cybersecurity training programme for all employees to reduce human-related security vulnerabilities and maintain an informed, vigilant workforce.
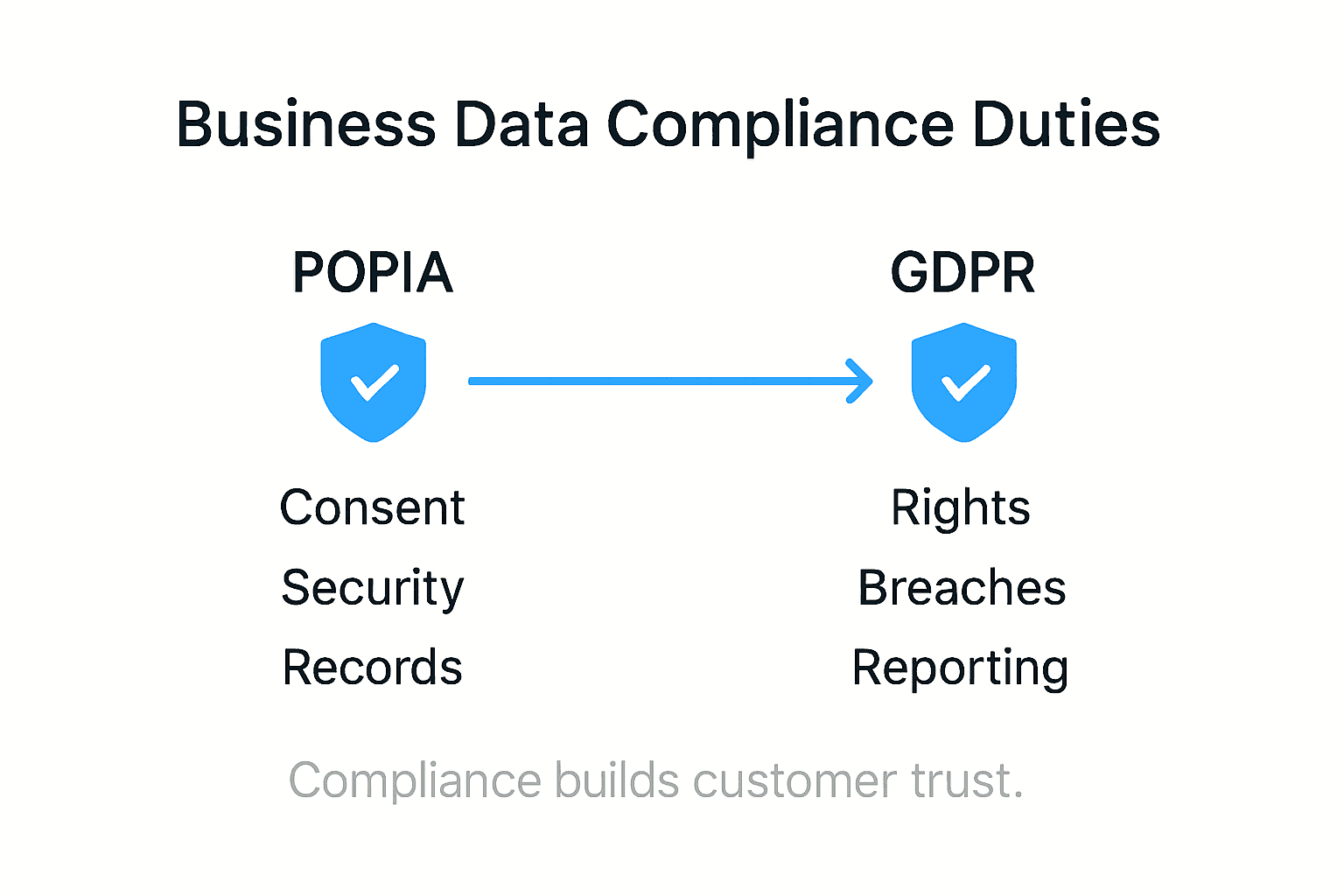
POPIA, GDPR and Global Compliance Duties
Navigating the complex landscape of data protection regulations has become a critical challenge for businesses operating in the digital realm. Understanding GDPR compliance for websites represents a crucial first step in protecting both organisational and customer data across international boundaries.
Two primary regulatory frameworks demand significant attention from South African businesses:
- Protection of Personal Information Act (POPIA): South Africa’s comprehensive data protection legislation
- General Data Protection Regulation (GDPR): European Union’s stringent data privacy framework
Both POPIA and GDPR share fundamental principles that require businesses to:
- Obtain explicit consent for data collection
- Implement robust data protection mechanisms
- Provide transparent information about data usage
- Enable individuals to request data deletion
- Maintain comprehensive records of data processing activities
- Report data breaches within specified timeframes
Compliance is not merely a legal requirement but a critical trust-building mechanism with customers. Organisations must develop comprehensive strategies that go beyond basic regulatory checklists, embedding data protection into their core operational processes. This involves creating clear data management policies, conducting regular privacy impact assessments, and training employees on the nuanced requirements of these regulations.
Pro tip: Develop a centralised data governance framework that can adapt to multiple international regulatory requirements, ensuring seamless compliance across different jurisdictions.
Here’s a concise comparison of POPIA and GDPR requirements for South African businesses:
| Requirement | POPIA Focus | GDPR Focus |
|---|---|---|
| Consent | Explicit for personal data | Explicit, informed consent |
| Data Breach Notification | Report within a reasonable time | Notify within 72 hours |
| Data Subject Rights | Access, correction, deletion | Access, rectification, erasure |
| Cross-Border Transfers | Requires adequate safeguards | Restrictions, adequacy assessment |
| Enforcement Authority | Information Regulator | European Data Protection Board |
Effective Defence Strategies and Best Practices
Cybersecurity defence demands a comprehensive, multi-layered approach that goes beyond traditional security measures. Implementing a data-driven framework for predictive threat detection has become essential for modern organisations seeking robust protection against evolving cyber threats.
Key defence strategies include:
- Zero-Trust Architecture: Verify every access request, regardless of origin
- Multi-Factor Authentication (MFA): Implement multiple verification layers
- Regular Security Audits: Conduct comprehensive system vulnerability assessments
- Automated Threat Monitoring: Utilise AI-powered detection and response systems
- Continuous Employee Training: Build a human firewall through awareness programmes
A defence in depth strategy requires organisations to create multiple protective layers that work synergistically. This means implementing technical controls, administrative policies, and physical security measures that collectively create a comprehensive protection ecosystem. Technical solutions should be complemented by robust employee training programmes that transform staff into active participants in the organisation’s cybersecurity defence.
Successful cybersecurity is not about preventing every possible attack, but developing an adaptive, resilient system that can quickly detect, respond to, and mitigate potential breaches. This requires ongoing investment in technology, personnel skills, and organisational processes that can evolve alongside emerging cyber threats.
Pro tip: Develop a dynamic incident response plan that includes clear escalation protocols, ensuring your team can react swiftly and effectively to potential security breaches.
Human Risk, Staff Training and Avoiding Mistakes
Cybersecurity awareness training has become critical as human error accounts for 95% of cyber breaches, transforming employees from potential vulnerabilities into a robust first line of defence. Understanding and mitigating human risk requires a comprehensive approach that goes far beyond traditional technical security measures.
Key areas of human cybersecurity risk include:
- Social Engineering: Recognising manipulative techniques designed to extract sensitive information
- Password Management: Creating and maintaining strong, unique credentials
- Phishing Awareness: Identifying suspicious emails, links, and communication attempts
- Data Handling Protocols: Understanding proper procedures for sensitive information
- Incident Reporting: Knowing how and when to escalate potential security threats
Effective staff training programmes must be dynamic, engaging, and continuous. This means moving beyond annual compliance workshops to create interactive, scenario-based learning experiences that simulate real-world cyber threats. Organisations should implement regular simulated phishing tests, cybersecurity workshops, and personalised feedback mechanisms that help employees develop an instinctive understanding of potential risks.
Technology can complement human training through behavioural monitoring systems and intelligent alerting mechanisms. By combining technical controls with comprehensive education, businesses can create a human firewall that actively protects against potential security breaches. The goal is not to blame or punish employees but to empower them with knowledge and tools to make informed security decisions.
Pro tip: Implement quarterly interactive cybersecurity training sessions with practical scenarios and immediate feedback to keep security awareness fresh and engaging.
This table summarises staff training elements and their benefits for cybersecurity:
| Training Element | Benefit to Business |
|---|---|
| Simulated Phishing | Reduces risk of email-based attacks |
| Password Workshops | Strengthens credential management |
| Data Handling Drills | Minimises accidental information leakage |
| Incident Reporting | Ensures rapid response to threats |
Choosing Security Solutions for Business Needs
Selecting appropriate cybersecurity solutions requires a strategic approach that matches technological capabilities with specific organisational vulnerabilities. Businesses cannot adopt a one-size-fits-all strategy but must develop a nuanced security ecosystem tailored to their unique operational landscape.
Critical components of an effective security solution portfolio include:
- Endpoint Protection: Comprehensive defence for individual devices
- Network Firewalls: Robust perimeter security mechanisms
- Zero-Trust Architectures: Continuous authentication and verification
- Threat Intelligence Systems: Proactive risk identification platforms
- Managed Security Services: External expertise and continuous monitoring
Successful security solution selection demands thorough organisational assessment. This involves conducting comprehensive risk assessments, understanding regulatory requirements, evaluating existing technological infrastructure, and determining potential financial investment capabilities. Modern businesses must consider scalability, integration potential, and adaptive capabilities when choosing security technologies.
Technology selection is only the beginning. Organisations must develop robust implementation strategies that include staff training, ongoing monitoring, periodic system reviews, and adaptive response protocols. The most sophisticated security solutions become ineffective without proper human understanding, continuous refinement, and organisational commitment to maintaining a proactive security culture.
Pro tip: Conduct an annual comprehensive cybersecurity infrastructure audit to ensure your security solutions remain aligned with evolving technological landscapes and emerging threat vectors.
Strengthen Your Business Cybersecurity with Tailored Digital Solutions
In today’s digital landscape, safeguarding your business against evolving cyber threats and ensuring compliance with laws like POPIA and GDPR are urgent priorities. The article highlights critical pain points such as managing human risk, implementing multi-layered defence strategies, and embracing proactive cybersecurity measures. Achieving this requires not only awareness but also a robust, custom-built digital infrastructure designed to protect your data and customer trust.
At Cloud Fusion, we specialise in delivering bespoke web and mobile applications that incorporate cutting-edge security features aligned with your specific business needs. Our full-service approach includes strategic branding, secure web design, and scalable cloud solutions, empowering your organisation to stay resilient against cyber-attacks. Don’t leave your digital presence vulnerable. Explore our Web Design and Development Quotation to begin crafting a secure, compliant, and future-ready platform.
Take action now to fortify your defences and ensure regulatory compliance. Partner with Cloud Fusion to build a seamless security framework integrated with your digital assets. Visit Cloud Fusion’s solutions today and discover how a customised, secure online presence can protect your business and build lasting customer confidence.
Frequently Asked Questions
What are the key components of a comprehensive cybersecurity strategy for businesses?
A comprehensive cybersecurity strategy should include risk assessment strategies, advanced technological infrastructure, robust personnel training programs, and continuous monitoring and adaptation to evolving threats.
How can businesses mitigate human-related cybersecurity vulnerabilities?
Businesses can mitigate human-related vulnerabilities by implementing regular cybersecurity awareness training for employees, developing strong password management practices, and creating clear data handling protocols to minimize risks associated with human error.
What are the most common types of cyber threats that e-commerce firms face?
E-commerce firms commonly face threats such as phishing attacks targeting credentials, malware infections damaging systems, denial-of-service (DoS) attacks disrupting operations, and personal data breaches involving unauthorized access to sensitive customer information.
How can organizations ensure compliance with data protection regulations like POPIA and GDPR?
Organizations can ensure compliance by obtaining explicit consent for data collection, implementing robust data protection mechanisms, conducting regular privacy impact assessments, and developing a centralized data governance framework that adapts to various regulatory requirements.








