More than 80 percent of South African companies now rely on the cloud for storing sensitive business data and running daily operations. As businesses embrace digital transformation, understanding cloud security becomes vital to protect assets and comply with evolving legal demands. This guide breaks down the core cloud security concepts that every South African organization needs to navigate risks, stay compliant, and defend valuable information against modern threats.
Table of Contents
- Core Cloud Security Concepts Unpacked
- Key Types of Cloud Security Solutions
- Cloud Threats, Vulnerabilities and Risks
- Best Practices for Business Cloud Protection
- Compliance, Data Privacy and Legal Needs
Key Takeaways
| Point | Details |
|---|---|
| Cloud Security Essentials | Effective cloud security requires a focus on confidentiality, integrity, and availability to protect sensitive information and maintain system accessibility. |
| Multi-Layered Security Approaches | Organisations should implement comprehensive security solutions, including Identity and Access Management and Data Encryption, to address various threats and vulnerabilities in cloud environments. |
| Continuous Compliance and Adaptation | Ongoing assessment of legal and regulatory standards is crucial for businesses to ensure compliance, particularly with frameworks like POPI and GDPR. |
| Proactive Risk Management | A dynamic, continuous risk management strategy is essential for identifying and mitigating emerging threats in cloud computing scenarios. |
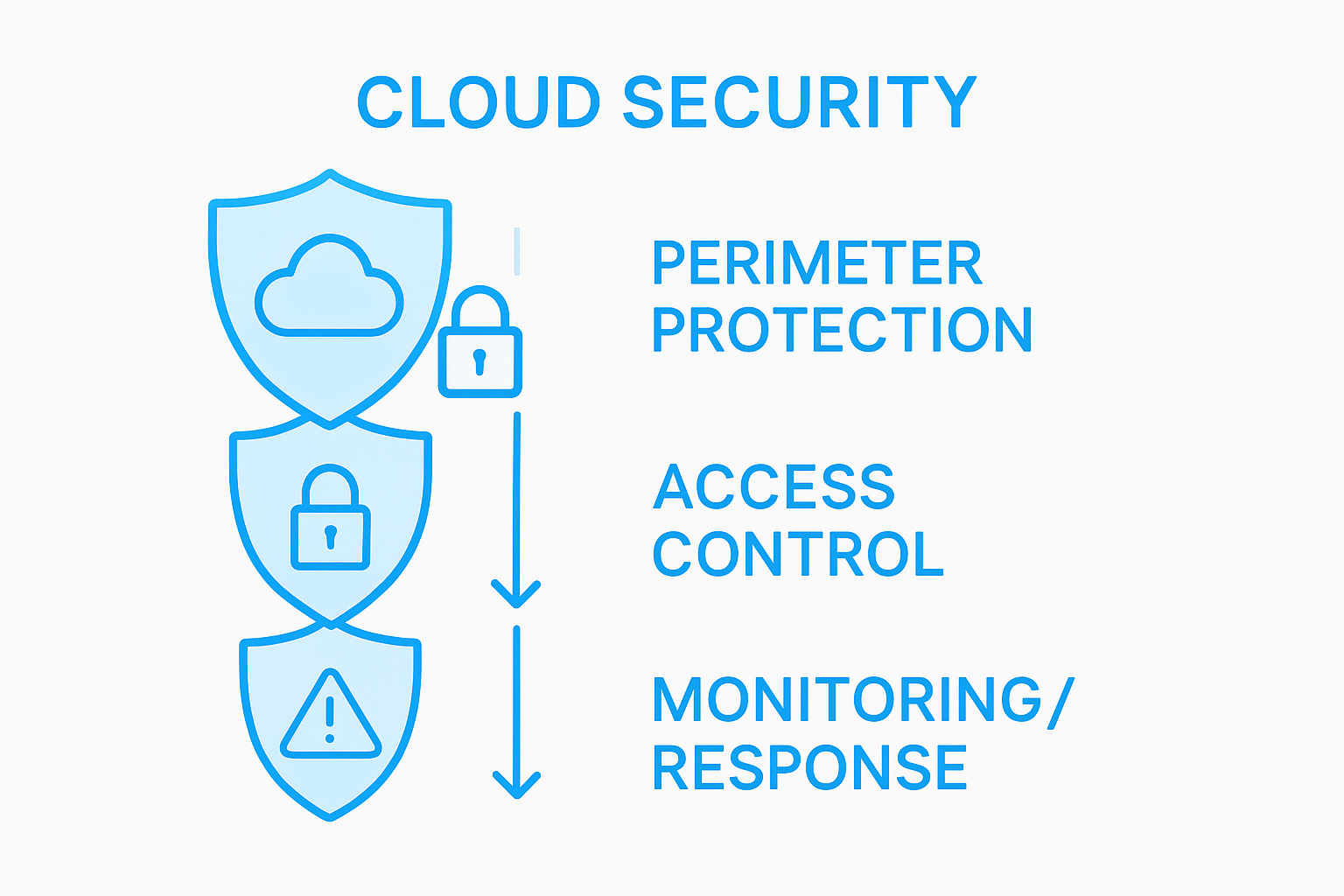
Core Cloud Security Concepts Unpacked
Cloud security represents a strategic approach to protecting digital assets, infrastructure, and information systems deployed across cloud environments. Cloud security fundamentals encompass multiple critical dimensions that organisations must comprehensively understand to safeguard their technological investments.
At its core, cloud security involves managing three primary risk domains: confidentiality, integrity, and availability. Businesses must implement robust mechanisms to protect sensitive data from unauthorised access, ensure information remains unaltered during transmission and storage, and guarantee consistent system accessibility. Strategic deployment models help organisations navigate these complex security requirements across different cloud service architectures.
Key cloud security concepts include:
- Identity and Access Management: Controlling user permissions and authentication
- Data Encryption: Protecting information during transit and at rest
- Network Security: Implementing firewalls, intrusion detection systems
- Compliance Frameworks: Adhering to industry-specific regulatory standards
Successful cloud security strategies demand a holistic approach that integrates technological solutions, comprehensive policies, and ongoing risk assessment. Organisations must continuously evaluate their cloud infrastructure, adapting security protocols to address emerging technological threats and protect their digital ecosystem.
Key Types of Cloud Security Solutions
Cloud security solutions represent sophisticated technological frameworks designed to protect digital infrastructure across various computing environments. Comprehensive defense mechanisms have emerged to address the complex security challenges facing modern organisations.
One critical security solution is the Cloud Access Security Broker (CASB), which operates as an intermediary monitoring platform between cloud service users and their applications. Cloud access security brokers provide essential services including:
- User activity monitoring
- Policy compliance enforcement
- Malware prevention strategies
- Real-time threat detection
Additional key cloud security solutions include:
- Identity and Access Management (IAM): Controls and manages user permissions
- Encryption Services: Protects data during transmission and storage
- Network Security Platforms: Implements firewalls and intrusion detection systems
- Compliance Management Tools: Ensures adherence to industry regulations
Modern organisations must adopt a multi-layered cloud security approach that integrates technological solutions, comprehensive policies, and continuous risk assessment. By implementing robust security frameworks, businesses can effectively protect their digital assets while maintaining operational flexibility and innovation potential.

Cloud Threats, Vulnerabilities and Risks
Cloud computing environments present complex security challenges that demand sophisticated risk management strategies. Virtualized infrastructure security reveals multiple potential vulnerabilities within cloud architectural layers that organisations must carefully address.
Cybersecurity threats in cloud environments can be categorised into several critical domains:
- Infrastructure Vulnerabilities: Risks associated with hypervisor and virtualisation layers
- Data Exposure Risks: Potential unauthorised access and information breaches
- Access Control Challenges: Authentication and permission management weaknesses
- Compliance and Regulatory Risks: Potential violations of data protection standards
Emerging cybersecurity information requirements highlight significant transformations in cloud security, including essential considerations such as:
- Data-asset decoupling mechanisms
- Resource dependency tracking
- Comprehensive data provenance management
- Advanced threat detection protocols
Website security best practices suggest that organisations must adopt a proactive, multi-layered approach to cloud security. By implementing robust monitoring, continuous risk assessment, and adaptive security frameworks, businesses can effectively mitigate potential threats while maintaining operational efficiency and technological innovation.
Best Practices for Business Cloud Protection
Cloud security demands a comprehensive and strategic approach that goes beyond traditional IT protection methodologies. Cloud security frameworks provide essential guidelines for organisations seeking robust digital infrastructure protection.
Key best practices for comprehensive cloud protection include:
- Continuous Risk Assessment: Regular vulnerability scanning and threat analysis
- Multi-Factor Authentication: Implementing advanced access control mechanisms
- Data Encryption: Protecting sensitive information during transmission and storage
- Comprehensive Monitoring: Real-time threat detection and incident response
Cloud computing security strategies highlight critical implementation considerations such as:
- Understanding potential attack vectors
- Developing adaptive defence mechanisms
- Creating resilient architectural designs
- Establishing robust compliance protocols
Online business security compliance emphasises the importance of integrating regulatory requirements into cloud protection strategies. Successful organisations recognise that effective cloud security is not a one-time implementation but an ongoing, dynamic process requiring continuous adaptation, skilled personnel, and advanced technological solutions.
Compliance, Data Privacy and Legal Needs
Cloud computing compliance represents a complex landscape of regulatory requirements that vary significantly across different industries and jurisdictions. Cloud security compliance frameworks provide essential guidelines for organisations navigating legal and regulatory challenges in digital environments.
Key compliance considerations for businesses include:
- Industry-Specific Regulations: Tailored requirements for healthcare, finance, and retail sectors
- Data Protection Standards: Adherence to POPI, GDPR, and international privacy laws
- Cross-Border Data Management: Managing legal complexities of international data transfers
- Audit and Reporting Mechanisms: Demonstrating regulatory compliance
Cybersecurity information requirements highlight critical aspects of data management such as:
- Comprehensive data provenance tracking
- Resource dependency documentation
- Advanced information governance protocols
- Transparent data handling mechanisms
GDPR Compliance Guidelines emphasise the importance of proactive legal strategy. Successful organisations must view compliance not as a static checkbox exercise, but as a dynamic, ongoing process that requires continuous adaptation, technological sophistication, and a deep understanding of evolving regulatory landscapes.
Strengthen Your Business Innovation with Tailored Cloud Security Solutions
Securing your digital assets and ensuring compliance are vital challenges highlighted in “Cloud Security Essentials – Safeguarding Business Innovation.” Many businesses struggle to maintain confidentiality, integrity, and availability of data while adapting to evolving cloud threats and compliance requirements. Without a well-rounded strategy including multi-factor authentication, continuous risk assessments, and proactive monitoring, your organisation could face serious vulnerabilities that threaten innovation and growth.
At Cloud Fusion, we understand these pain points and offer custom, scalable digital solutions designed to fortify your cloud environment. Our expertise covers secure web development and comprehensive cloud services combining strong identity and access management with robust encryption. Explore how our solutions can integrate compliance frameworks and advanced security measures that protect your sensitive data and help you focus on expanding your business.
Ready to safeguard your business against emerging cloud risks and build a resilient online presence? Take the next step by requesting a bespoke web design and development quotation. Discover how our full-service approach will support your digital transformation and keep your cloud infrastructure secure. Visit Cloud Fusion today and start securing your future with confidence.
Frequently Asked Questions
What are the key components of cloud security?
Cloud security primarily involves managing three risk domains: confidentiality, integrity, and availability. Essential components include Identity and Access Management (IAM), data encryption, network security, and compliance frameworks to protect data from unauthorized access, maintain information integrity, and ensure system accessibility.
How does a Cloud Access Security Broker (CASB) enhance cloud security?
A CASB acts as an intermediary monitoring platform between users and cloud applications. It provides essential services such as user activity monitoring, policy compliance enforcement, malware prevention strategies, and real-time threat detection, enhancing overall cloud security posture.
What are some best practices for protecting cloud data?
Best practices for cloud protection include continuous risk assessment, implementing multi-factor authentication, encrypting sensitive data during transmission and at rest, and employing comprehensive monitoring for real-time threat detection and incident response.
How can businesses ensure compliance with cloud security regulations?
Businesses can ensure compliance with cloud security regulations by adhering to industry-specific regulations, following data protection standards like POPI and GDPR, managing cross-border data transfers carefully, and implementing robust audit and reporting mechanisms to demonstrate regulatory compliance.








